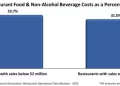
Nonetheless you deal with your informationpay transactions, payroll and human assets data, stock administration, or loyalty applicationscybercriminals and hackers can assault you the place youre most susceptible.
Phishing, ransomware and malware are simply among the methods cyberthieves can entry and steal your helpful information. Restoration is priceyfinancially and in lack of popularity.
To assist restaurateurs keep away from information breaches and the troubles they convey, the Nationwide Restaurant Affiliation tailored the National Institute for Standards and Technologys Framework for Enhancing Essential Infrastructure Cybersecurity.
Two guidesa 101 base intro to cybersecurity and the deeper-dive 201 particularly tailor-made to cybersecurity for restaurant operatorshave been initially launched in 2017, and have been primarily based on NIST 1.0. The Affiliation up to date 101 in 2020, and now debuts 201, which was tailored to mirror NIST 1.1.
Digital Safety 101 examines the NIST Frameworks 5 core capabilities, and presents fast overviews of the right way to:
- Determine vulnerabilities in your methods, personnel entry, software program and {hardware}.
- Defend towards these dangers.
- Detect assaults in your laptop methods and networks earlier than the harm is finished.
- Reply to a knowledge breach or cyberattack in your methods or networks.
- Get well quicker after responding to a knowledge safety incident.
Digital Safety 201 showcases intimately the important thing steps restaurant IT personnel ought to think about when placing a cybersecurity plan collectively, score them on a scale of criticality from Pressing to Complementary.
The replace displays new additions to the NIST 1.1 Framework, equivalent to:
- The vital necessity for multi-factor authentication in transactions and information entry
- A brand new part to Determine protocols that allow you to vet the safety of supply-chain companions
The next are examples from every of the 5 capabilities deemed Pressing to finish in your cybersecurity setup protocols:
IDENTIFY
Youve mapped out how your organizational communications and information circulation
Inquiries to ask: Has somebody with IT expertise diagrammed how data strikes by way of your operation? For instance, bank card data strikes from POS gadget to server to processor, and many others. Has an IT professional drafted community diagrams? Have these been up to date? Who has entry to them?
Anticipated outcomes when you full this motion: Your operation ought to put together and periodically replace a doc describing the data circulation inside the enterprise and the way IT software program, {hardware}, and personnel help that data circulation. The doc ought to describe how this data helps your corporation and describe the relative danger to the enterprise if this data is compromised.
PROTECT
You’re managing distant entry
Inquiries to ask: Are you managing distant entry to your methods? Do you require third-party suppliers to make use of distinctive, particular person logins? Are you managing third-party information connectivity? Are you limiting third-party entry to solely these methods they should entry? Do you retain a log of whos accessing your system?
Anticipated outcomes when you full this motion: Distant entry consists of inner enterprise connections, service suppliers and third-party information connections. All these connections ought to require distinctive credentials for every person with entry. All entry must be restricted to solely the {hardware}, functions or information required. All actions carried out remotely must be logged. All entry to the Cost Card Business (PCI) cardholder information community ought to require two-factor authentication.
DETECT
You’re monitoring methods to detect potential information safety occasions
Inquiries to ask: Are you monitoring your community to detect potential cybersecurity occasions? Are you segmenting your networks primarily based on the classification ranges of saved data? Are you reviewing person accounts and disabling these which are now not getting used or are now not related to a enterprise course of? Do you encrypt delicate saved data and require a multi-factor authentication mechanism to entry it?
Anticipated outcomes when you full this motion: Protects data saved on methods with file system, community share, claims software or database-specific entry management lists. Solely approved people ought to have entry to the data. Displays account utilization to find out dormant accounts and notify the person or persons supervisor. Disables such accounts if not wanted, or paperwork and screens exceptions (e.g., vendor upkeep accounts wanted for system restoration or continuity operations). Requires that managers match energetic workers and contractors with every account belonging to their workers. Safety or system directors ought to then disable accounts not assigned to legitimate workforce members. Be sure that all account person names and authentication credentials are transmitted throughout networks through encrypted channels.
RESPOND
You execute your response plan throughout or after an incident
Inquiries to ask: Do you will have a response plan and are you following it?
Anticipated outcomes when you full this motion: If in case you have a plan in place, the consequences of cybercrime might be shorter, your response might be extra organized, and your exterior and inner clients are more likely to be extra glad that you’re taking the mandatory steps to resolve the breach.
RECOVER
You’re managing public relations
Inquiries to ask: Are you managing the general public relations fallout from the incident?
Anticipated outcomes when you full this motion: Prospects totally perceive that you’re doing all the pieces you may to mitigate the occasion.
Digital Security 201 is sponsored by Dell Applied sciences